Automate Your Snowflake Access Controls
How we use recommendations to simplify and secure your Snowflake data.
Let's face it: dealing with access controls is the last thing any data team wants to spend their time on. But what if we told you that managing access could be simple?
Spyglass’s mission is to make access management secure and simple for data teams.
So how exactly do we make “simple” happen?
Enter: Spyglass Recommendations
Spyglass Recommendations provide an automated analysis of existing roles and policies with proactive suggestions, including one-click DDL updates.
While Spyglass also provides the ability to understand who can access what (by table, schema, role, etc.), access policy controls and “self-service” data access workflows, what can be most valuable is the awareness of where to focus your efforts.
With Spyglass, you’ll discover problems, fix them, and then set up automated remediation so you don’t have to think about access management on a daily basis (we’ll walk through this automation later).
Is Access Management Your Core Competency?
Unless you’re one of a handful of security companies, access management is not part of your core business. These controls are not unique to your business — and if you are able to build tools that are world-class — you’ve likely already wasted your time. Well… at least you’ll have a nice presentation for the next trade show.
While access management may not be core to your business, it’s still important to get right.
The number one issue in the OWASP Top Ten is broken access control (for example, misconfigured policies), meaning that users can act outside of their intended permissions.
Whether you like it or not, the data you manage from your customers… is your liability.
GRANT ALL PRIVILEGES ON DATABASE tatooine TO ROLE galactic_empire;
GRANT ROLE weapon_systems_viewer TO USER darth_vader;An Ounce of Prevention…
Most troublesome is when teams don’t know when an access issue is occurring. This could put your team at risk in the context of GDPR, SOX, CPRA and other access defined compliance measures. The common scenarios we see data teams face specific to access controls:
Unaware of problem + proficiency to fix
Unaware of problem + unable to fix
Awareness of problem + no proficiency to fix
Awareness of problem + proficiency to fix
A significant part of access engineering is not just having the tools to fix problems, but also the insights to know there is a problem in the first place.
It’s rare that a team cannot fix an access issue, but also rare that they are aware of existing gaps in access to begin with.
What if when you configured access, you knew immediately whether you made a mistake?
Well, with a little insight into how to set up access correctly at the time of configuration, the majority of common problems can be avoided.
And even when you know how to fix the issue, that issue is likely to occur again and again. Your data and users are not static, but change frequently.
Solving Issues at Scale
We’ve yet to find a data team that gets excited about dealing with access controls. So solving all of these problems, even if you are capable of running the (hundreds of) SQL commands yourself, is a win for your time and your team's security.
Summarizing our learnings on access management early on building Spyglass:
Managing access is complex (design, implementation, and maintenance)
Data teams don’t want to manage access (not a revenue driver or unique to the business)
Access controls become exponentially untenable as teams scale (number of users, roles, and objects across multiple accounts)
The final learning is that data teams want to be told how to fix these access problems. To quote from many of our meetings, “Just tell me what to do!”
While we had tools and features available in Spyglass to fix problems, we realized we needed to provide a more opinionated and prescriptive workflow that would proactively do the work for you.
As we started to build Recommendations, we intentionally created a solution that first cleans up existing access (as teams typically have access debt they need to correct) and second provides “guardrails” and an operational cadence for consistent access moving forward.
Diving Deep on Recommendations
Now, let’s walk through the basics of Recommendations.
While the below example shows the Spyglass UI, the ability to apply Recommendations to your access configurations is available in the CLI as well.
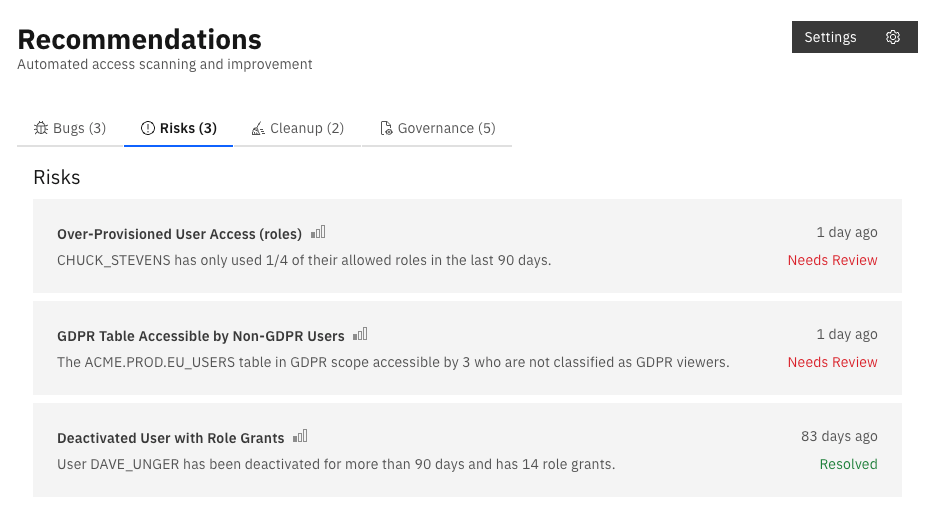
Once Spyglass is set up in your Snowflake admin console, Recommendations will audit your existing Snowflake access controls and provide insights on what we classify as bugs (misconfigurations), risks (insecure access), cleanup (duplicate access) and governance (access related to ownership) as seen below.
Clicking into any single Recommendation provides a summary of a recommended fix along with a proposed (editable) and final DDL change that takes one click to update.
Diving into the settings, as we’ve released Recommendations, we’ve added to our library based on customer requests and specific use cases. You can see a sampling of these below.
Spyglass also provides workflows or additional automation to trigger actions based on a Recommendation (e.g. if a deactivated user for more than 90-days is detected, then automatically delete the user) along with rule based alerts (e.g. if any user is granted ACCOUNT ADMIN, then send an alert).
Recommendations in the CLI
Before we wrap up, a quick look on these same configurations in our CLI:
To simplify in the words of a customer, “We want access controls to be so easy that our interns can manage access..instead of our Staff Engineers.” Well… here you go. Turn your interns into Jedi Knights.
Recommendations Rewind
Spyglass Recommendations corrects existing policies and provide safeguards for continuous enforcement moving forward, so you can secure your database and get back to building.
If you’ve nodded your head while reading this, reach out at spyglass.software (or demo@spyglass.software) and we’ll show you a product demo to give you a taste of the future of data access management.