Motivation
Managing Snowflake roles at scale is challenging — and you’d rather be solving the hard problems of your business, not dealing with the day-to-day issues of users missing access.
Enter Data GovOps, combining strong governance with efficient ops.
Governance describes the centralized methods to proactively control, analyze, and improve your IAM access stack with insights, recommendations, and governance workflows.
Operations describes the distributed methods to enable self service with approval workflows, temporary access control, and row and column-level management.
Governance
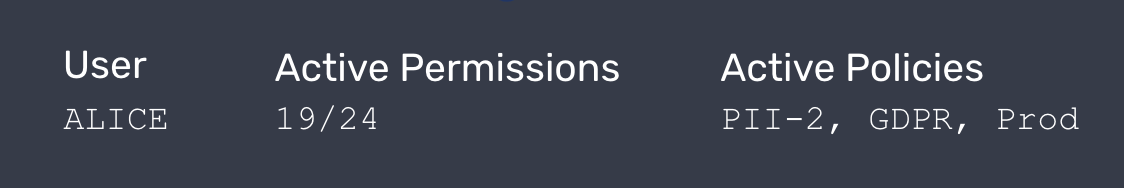
Permission Analysis
Permissions define who can access what. But these access patterns are a continuously shifting ocean of complexity. At a high level, it’s important to understand:
Over-provisioned Access — Are users actually using the permissions they’ve been assigned (over some reasonable time period)?
Anomalous Access — Are users accessing data that is materially different from other users in their job function?
In Scope Policies — What business specific (compliance) policies are users in scope of that will impact their clearance levels?
In-depth permission analysis helps your data team and security teams understand and investigate user access, roles, and object relationships across all of your databases and accounts.
Insights and Recommendations
It’s really easy to create roles, it’s harder to clean them up.
Understanding your access landscape is the first step to improving it. The next step is intelligent recommendations:
Duplicate Roles — Which roles have overlapping responsibilities?
Unused Roles — Which roles haven’t been used recently?
Misconfigured Roles — Which roles are incorrectly formed? For example, does a role grant access to a table, but not the parent database or schema?
A solid security posture means continuous access control monitoring and remediation, proactive guidance paired with suggested adjustments to improve access rules.
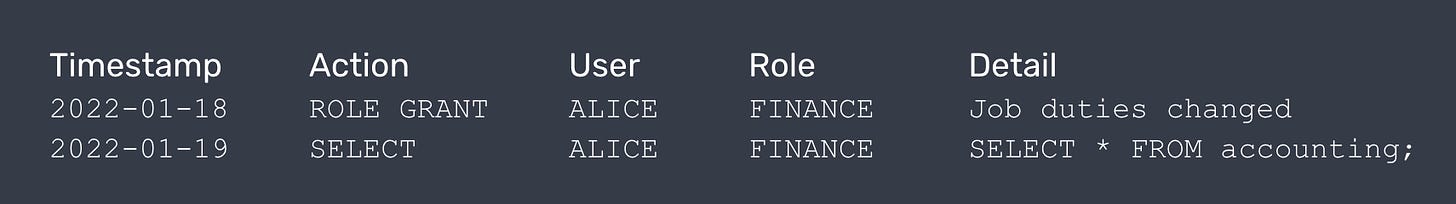
Comprehensive Audit Trial
Snowflake’s Query History and Access History offer the details of user access behaviors, but have limited retention periods. They also lack context around changes in access control.
Your governance solution should record and document every access configuration and change request, plus detail around when, how, and why the change was made.
In addition, your audit trail should have rules for determining what kinds of access should be archived with a longer retention period. Maybe you want to record everything forever; or, more realistically, maybe you just want to record any and all queries made to PII-related tables for 5 years.
Operations
Access Request Workflows
GovOps puts power in the hands of users by offering self service access request workflows. In short, the ability for users to request temporary (e.g. break glass) access for data for valid business reasons.
Customizable governance rules enable non-technical governance, compliance, and security users to be involved in the decision-making loop.
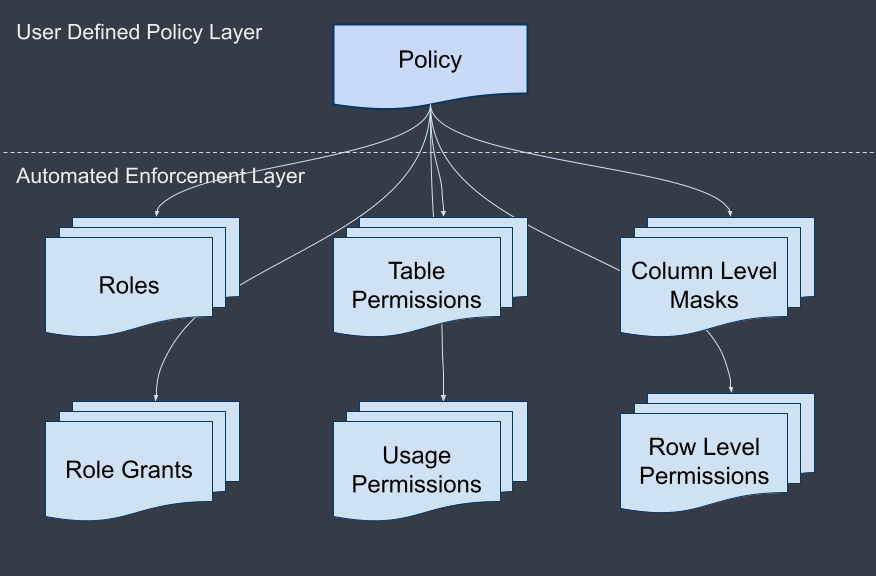
Policy Driven Controls
Ideally, your GovOps framework supports team oriented access policies like “members of the finance team can read finance data,” as well as more compliance oriented policies like “GDPR scoped users can request short-lived access to GDPR scoped data,” plus everything in between.
From there, automation should create the appropriate roles, permissions, and grants to enforce that policy.
This is what it means to be policy driven.
First, your team defines high level “who can access what” policies. Then, software handles the painstaking detail of creating enforcement rules to match that policy.
Policy driven controls are a powerful construct for securing your PII data that is in scope of compliance initiatives like GDPR, SOC2, HIPAA, and CCPA, and ensuring that access is controlled at the row and column levels.
ABAC and RBAC Support
While role-based access control has been standard practice for the last decade or two, attribute-based access control has surged in interest in recent years.
RBAC is often good enough in the early chapters of your access story, but we’ve seen growing demand for ABAC as the “plot thickens” in your data narrative.
GovOps isn’t opinionated about one form of access control over the other, in fact it’s more geared towards picking the tool that fits for at your stage of data platform adoption.
About Spyglass
Since you’re here, let me tell you what we’ve cooked up at Spyglass. In short, we make Snowflake data access controls easy - or provide an automated and better way to do the above.
If you’ve nodded your head while reading this, reach out at spyglass.software (or demo@spyglass.software) and we’ll show you a product demo to give you a taste of the future of data access management.